Cyber Operators Course (Op) – Module 2
Accidental `Self-Hack` – Password Manager Applications
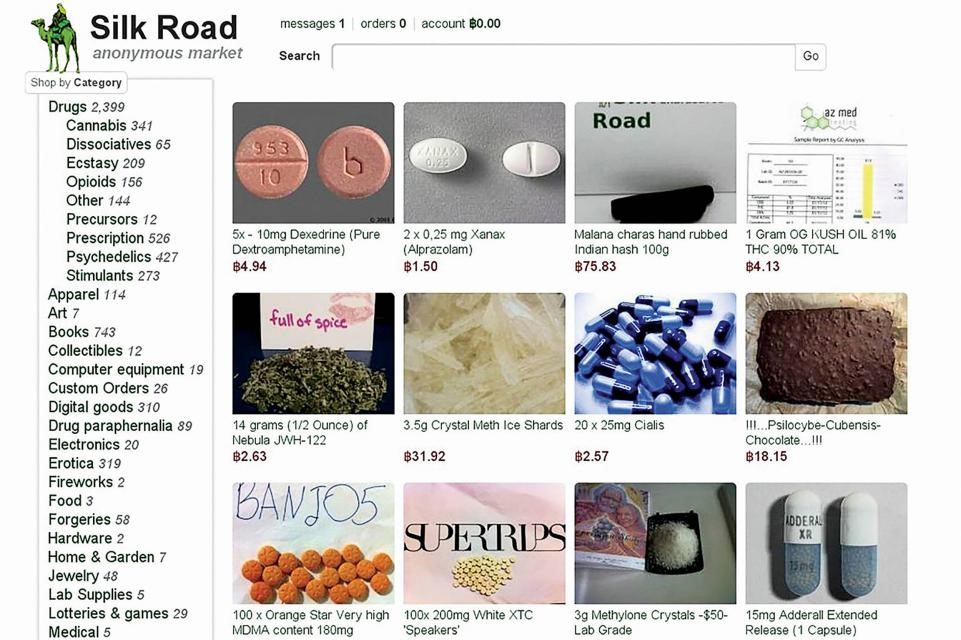
There is plenty on the internet about creating strong passwords. A common view is that passwords should be created and stored in a password manager application.
Passwords managers are simple, free for personal use and store passwords safely. Instead of the user having to remember multiple complex passwords, which usually leads to re-use, the password manager handles it all. Unique, truly complex passwords are created!
.
*Images: There are many available on the market. However, it could simply be a log onboard, centrally managed in a secure location, with a list of when they need changing and what they have been changed to.